Wow, what a whirlwind the last few weeks has been. I have been in the road for several weeks and finally on the last flight before home. Travel is funny. It seems like a busy, hectic, whirlwind, but it is also a lot of time to sit and reflect with little interruption. Since leaving Bonn, I have been trying to put together my thoughts about all information, discussions, and ideas that took place over the three days.
My overall impression is: Damn! What a great group of individuals we have working on coreboot. It takes a lot of work to put together an event and Carl-Daniel and the BSI hosted a great event.
Day1
I was really surprised how many people attended Friday. It was a little intimidating walking into a room full of about 40+ people (maybe Carl-Daniel can give us some official numbers). I settled in saying hi to a few familiar faces before we got started for the morning talks. The morning and early afternoon talks were very good I won’t cover them all here, please see the agenda. Most of the topics seemed to have bits of things that setup for the topics I wanted to cover later in the afternoon.
I had several talks prepared this year and my overarching theme was about scaling and growing coreboot. I’ve participated in numerous upstream efforts from vendors like Google, Intel, AMD, and Sage for the last year or more and have seen the number of contributors go from a few individuals to dozens of dozens. The community has done a great job at digesting the huge amount of new code, members, and attention coreboot has received, but with the growth, we were starting to hit the limits of some of the current processes. Earlier in 2015, we’d made a number of changes to structure and organization, but we need to continue to formalize some processes and communication, so we can manage the influx of code and participation. Fortunately the community is very flexible and had already accepted most of this growth. I planned to discuss ways we can keep the flexibility, but add some light process to make community’s participation easier.
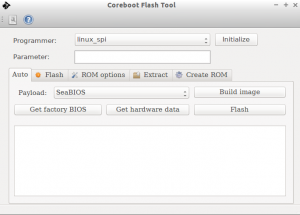
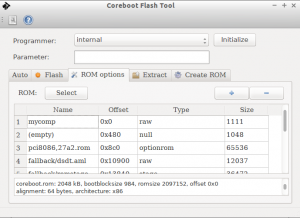
The topic of my first talk was the coreboot binary policy. What the community expects when contributing a binary to the separate 3rdparty/blobs repository. There seemed a general consensus that it was a good idea and discussion quickly went away from the policy and towards acceptance of a particular type of binary or if this policy would prevent vendors from pushing binaries. These were good points, but orthogonal to the need for instructing vendors what is expected by the community for binaries in the repository. The policy is still out for comment and review ( see post on the mailing list), but should be official shortly.
My second talk, with the help of Stefan and Patrick, was about working with vendors and some of the things we are doing to make the interaction easier. The main point was the coreboot versions and the quarterly release cycle, which had been announced in the spring. This cycle allows vendors and the community to plan feature releases and sync points to coordinate development.
The last talk of the day was presented by Stefan and me and was about the coreboot consortium and the progress is has made over the last year (which isn’t much). We are still stuck on it seeming like a good idea and vendors would like a consortium to exist, but we don’t have agreement on how and what should be done. This presentation was a call to action for the vendors that were present to engage the consortium and to get this ball moving for 2016.
It felt like I’d talked most of the day, but then it was off to dinner for some authentic regional German food and beer.
Day2
On the second day, we had a number of talks from David and Ron in California via Hangouts. I was impressed that it worked quiet well and kudos to those guys for staying up until 3am to present.
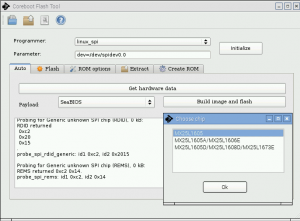
David’s talk on flashrom and the differences with the Chromium and flashrom source was really good. It seems that we may finally be able to re-merge the Chromium fork and that there will be some other changes to help flashrom get more participation. I think that it is moving to git and gerrit soon, and that there are just a few technical issues that should be sorted soon.
Ron like Go. That is all…. ;).
Actually, Ron’s talk on U-root was pretty cool. Read the paper: It U-root: A Go-based, Firmware Embeddable Root File System with On-demand Compilation https://www.usenix.org/system/files/conference/atc15/atc15-paper-minnich.pdf
Besides the topics, the hacking room was starting to fill up and a lot of side discussions and ideas were being thrown around. One funny memory was seeing the building security person poke his head in and see all the hardware and soldering station covering the tables and walk away with a grin and shaking his head.
In the afternoon Card-Daniel had organized a trip to the The Government Bunker (Regierungsbunker). A cold war relic and now a museum. It is a massive structure and an impressive tour. https://en.wikipedia.org/wiki/Government_bunker_(Germany)
Day 3
The last day was a focused hacking day. Again, lots of discussion and ideas for improvements and devices to port and hack on. I had an interesting conversation about mesh networks, German WiFi access rules, and the influx of refugees that are now arriving in Bonn. The volunteer maintained mesh networks allow the refugees to call home, find family, get news, and access the internet for services etc. There are rules in Germany about liability and responsibility of the WiFi access, so the mesh VPN to hubs that allow the clearing of that data. I found this all super interesting.
At the end of the day, I lead a discussion on community building and how coreboot can improve in 2016. The discussion was really good and very frank about some of the problems we are having (most of which people had been discussing in smaller groups all weekend). We came out of it with some specific actions we would like to do in 2015-2016.
Have more meetups (number 1 comment all weekend):
- Proposed hacker meetup in Paris around Fosdem
- 2016 in Bonn is probable
- Need a US meeting organizer, location, and date (San Jose, Boston, and Denver were mentioned)
Have more education:
- Create slides, talks, videos
- CCC hacker space talks and LUG talks
- New user landing page (not for developers)
- onboarding – coreboot install parties
- better wiki management/cleanup (find owner for the wiki?)
Add more testing (the second most talked about side topic this year):
- REACTS and LAVA actively investigated/developed
- Create a board-status disk image
- Add additional test
- gerrit/jenkins integration
Make an official gerrit policy:
- guidelines
- enforcement
- workflow
Form a coreboot consortium entity
There are a lot of other attendees, so I hope that they chime in with their experience. I’m sure I missed lots of stuff. As for my talks, I hope that they were helpful and everyone should feel free to send me feedback. Thanks again to Carl-Daniel and the BSI.
All the conference topics and other details are here: http://www.coreboot.org/Coreboot_conference_Bonn_2015